Beware: New ‘DeadLock’ Ransomware Weaponizes Polygon Smart Contracts to Stay Invisible

Cybersecurity researchers have gotten interested by a newly found ransomware pressure known as UselessLock that abuses Polygon sensible contracts to silently service its infrastructure and bypass standard detection instruments, as a current report by risk intelligence agency Group-IB depicts.
UselessLock, first noticed in July 2025, has up to now remained largely below the radar as a result of it doesn’t have a publicly dealing with associates program, it doesn’t have an information leak web site, and its victims have been linked to comparatively few confirmed victims.
That profile, nevertheless, covers a extra technologically subtle technique that researchers imagine is exhibiting a extra world change in the way in which cybercriminals are utilizing public blockchains for felony ends.
How UselessLock Hides Ransomware Infrastructure Inside Polygon Smart Contracts
Group-IB’s evaluation reveals that UselessLock makes use of sensible contracts deployed on the Polygon community to retailer and rotate proxy server addresses.
These proxies act as intermediaries between contaminated methods and the ransomware operators, permitting command-and-control visitors to shift endpoints with out counting on centralized infrastructure that may be seized or blocked.
By querying the smart contract, the malware retrieves the present proxy handle by means of a easy learn operation that leaves no apparent transactional footprint and incurs no community value.
Researchers mentioned this system mirrors earlier campaigns, akin to EtherHiding, disclosed final yr, wherein North Korean risk actors used the Ethereum blockchain to conceal and distribute malware payloads.
In each circumstances, public and decentralized ledgers had been was resilient communication channels which might be tough for defenders to disrupt. UselessLock’s use of Polygon extends that idea by embedding proxy administration instantly into a wise contract, permitting attackers to replace infrastructure on demand.

Once deployed, UselessLock encrypts information and appends a “.dlock” extension, alters system icons, and replaces the sufferer’s wallpaper with ransom directions.
Over time, the group’s ransom notes have advanced, with early samples referencing solely file encryption, whereas later variations explicitly said that delicate information had been stolen and threatened its sale if cost was not made.
The most up-to-date ransom notes additionally promise “added providers,” together with a breakdown of how the community was breached and assurances that the sufferer is not going to be focused once more.
This Ransomware Doesn’t Just Lock Files — It Opens a Chat With Hackers
Group-IB recognized at the least three distinct UselessLock samples from mid-2025, every exhibiting incremental modifications in techniques.
Analysis of related PowerShell scripts suggests the malware aggressively disables non-essential providers, deletes quantity shadow copies to stop restoration, and whitelists a restricted set of processes, notably together with AnyDesk
Investigators imagine AnyDesk is used as the first distant entry device throughout assaults, a discovering in keeping with separate digital forensics investigations.
A key component of UselessLock’s operation is an HTML file dropped on contaminated methods that embeds an encrypted session messenger interface. Victims can talk instantly with attackers by means of this file with out putting in further software program.
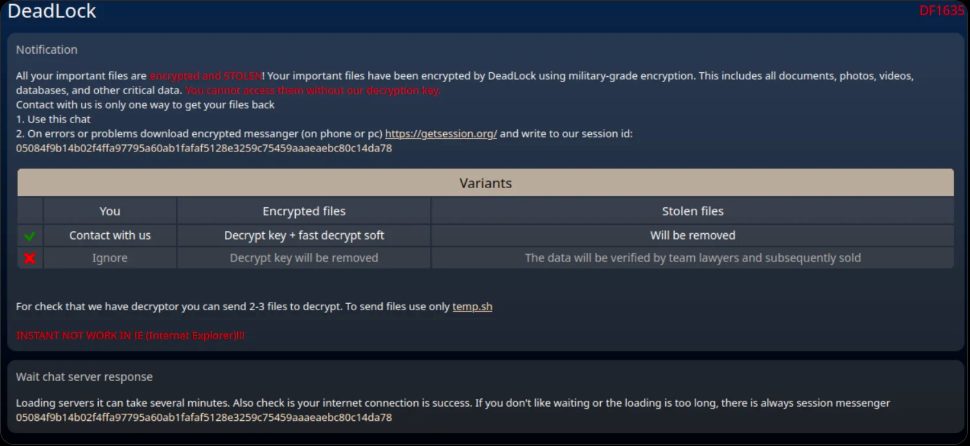
The embedded JavaScript retrieves proxy addresses from the Polygon smart contract, then routes encrypted messages by means of these servers to a session ID managed by the ransomware operators.
Transaction evaluation reveals that the identical pockets created a number of equivalent sensible contracts and repeatedly up to date proxy addresses by calling a perform labeled “setProxy.”
The pockets was funded by means of an exchange-linked handle shortly earlier than the contracts had been deployed, indicating deliberate preparation.
Historical monitoring of those transactions permits defenders to reconstruct previous proxy infrastructure, though the decentralized design complicates speedy takedown efforts.
The discovering is a part of an total improve in crypto-related cybercrime, as over $3.4 billion was stolen by hacks and exploits as of early December 2025, with state-linked North Korean teams accounting for over $2 billion of that complete.
The publish Beware: New ‘DeadLock’ Ransomware Weaponizes Polygon Smart Contracts to Stay Invisible appeared first on Cryptonews.

 UselessLock Ransomware: When Blockchain Meets Cybercrime
UselessLock Ransomware: When Blockchain Meets Cybercrime




