AI Ransomware Attacks Surge as Groups Leverage Automation to Target Victims – Is Your Crypto Secure?

Artificial intelligence (AI) has lowered the barrier to entry for cybercriminals, enabling ransomware teams to automate coding, generate polymorphic malware that alters its code with every an infection, and create convincing social engineering lures, in accordance to blockchain intelligence agency TRM Labs.
Nine rising teams recognized up to now 12 months have leveraged AI to scale their operations quickly, with some shifting away from encryption to depend on reputational harm, regulatory stress, and information leaks for extortion.
Global crypto scam losses surged to $4.6 billion in 2024, with at the least 87 AI-driven rip-off rings dismantled within the first quarter of 2025 alone.
According to Ari Redbord, Global Head of Policy at TRM Labs, “the road between financially motivated teams and state-linked actors can also be turning into more and more blurred”, with state-sponsored actors collaborating with cybercriminals to pool sources.
Most notably, TRM recognized APTLock as linked to the Russian state-sponsored group Fancy Bear, conducting damaging assaults that encrypt and delete information whereas defacing programs.
The group launders proceeds by means of lengthy peel chains with dozens of uniform-value deposits right into a non-custodial change, FixedFloat, earlier than changing to Monero.
AiLock, first recognized in April 2025, intentionally markets itself as AI-assisted and employs polymorphic malware for protection evasion.
The group threatens to report breaches to regulators and rivals whereas giving 72-hour response deadlines and five-day cost home windows.
AiLock launders funds by means of peel chain patterns, directing the bulk to the Wasabi mixer and routing smaller parts by means of FixedFloat.

Emerging Groups Deploy Tactics From Encryption to Pure Extortion
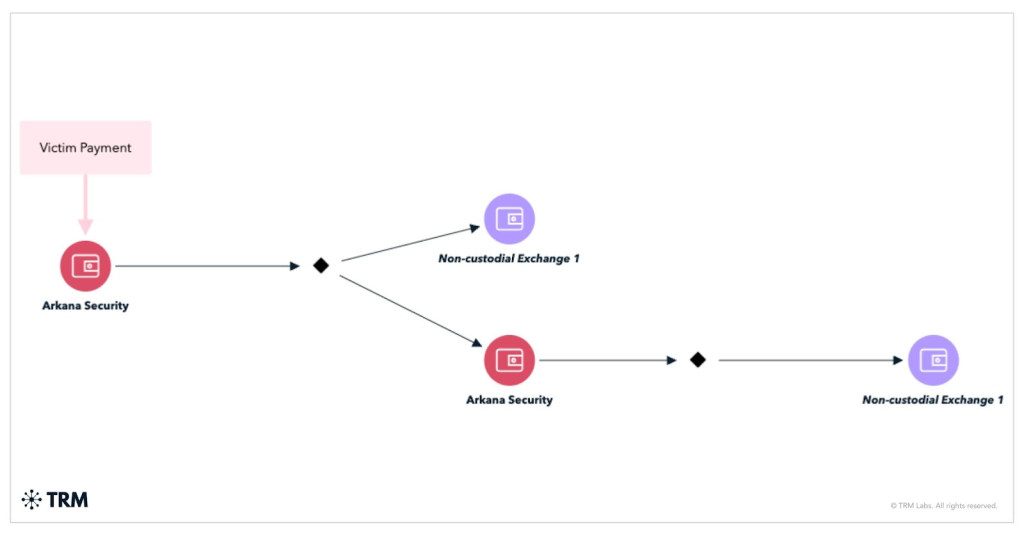
Among different notable teams, Arkana Security gained prominence after breaching U.S. cable supplier WideOpenWest in March 2025, using a three-phase extortion technique combining ransom calls for, information gross sales, and public leaks.
The group carries out assaults from phishing to credential theft and community lateral motion whereas doxxing executives’ personally identifiable data.
Arkana funnels all sufferer proceeds right into a single non-custodial change, creating probably recoverable cash-out patterns.
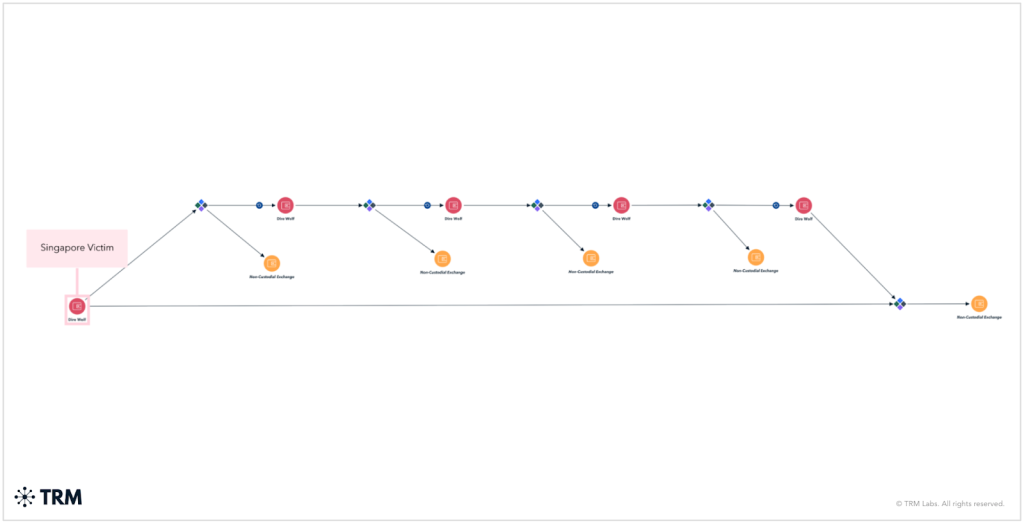
Notably as effectively, Dire Wolf conducts focused double-extortion assaults throughout manufacturing, know-how, healthcare, and development sectors, primarily concentrating on the United States and Thailand.
The group deploys customized Golang ransomware that disables safety instruments and deletes restoration recordsdata, directing victims to dwell darkish internet chatrooms for negotiations.
Proceeds are additionally laundered by means of a number of deposits into non-custodial exchanges to keep away from strict KYC procedures.
Similarly, Frag exploits the Veeam vulnerability rated CVSS 9.8, utilizing compromised VPN credentials with out multi-factor authentication to deploy ransomware with .frag extensions.
TRM assesses that Frag could also be related to the Akira ransomware group, as each make the most of shared pockets clusters and an identical cost providers.
The group expanded from its first sufferer in February 2025 to declare 27 organizations by March, with 25 of those situated within the United States.
On the opposite finish, Kairos operates in a different way by focusing solely on information exfiltration with out encrypting recordsdata, buying community entry from preliminary entry brokers.
Sophos discovered that solely half of ransomware assaults now contain encryption, the bottom degree in six years.
TRM recognized Kairos sharing cash-out addresses with SafePay, INC, Lynx, and Qilin ransomware teams, suggesting shared affiliate networks.
Deepfake Scams and Malware Campaigns Drain Millions From Users
Former Binance founder Changpeng Zhao lately issued urgent warnings following sophisticated deepfake Zoom attacks concentrating on the crypto neighborhood.
Japanese influencer Mai Fujimoto misplaced entry to her MetaMask wallets after a 10-minute video name with an AI-generated impersonation of an acquaintance whose Telegram account had been compromised.
Mehdi Farooq, a former Animoca Brands funding associate, additionally misplaced years of financial savings when six wallets have been drained after downloading faux Zoom software program throughout an identical deepfake name.
Crypto-stealing malware is spreading by means of faux AI, gaming, and Web3 startups with convincing web sites, social media profiles, GitHub repositories, and crew pages.
Darktrace identified schemes involving fake blockchain games, such as “Eternal Decay,” and startups together with Pollens AI, Swox, and Buzzu.
The malware targets Windows and macOS customers, stealing pockets credentials utilizing Realst and Atomic Stealer households with superior evasion methods, together with stolen software program signing certificates.
As a part of the continuing conflict in opposition to the rising menace, Spanish authorities recently dismantled a crypto investment scam that defrauded over 200 victims out of greater than €19 million utilizing AI-generated celeb movies to promote faux high-return ventures.
The investigation has arrested six people, aged 34 to 57, who’re dealing with expenses of fraud, cash laundering, and doc falsification.
The put up AI Ransomware Attacks Surge as Groups Leverage Automation to Target Victims – Is Your Crypto Secure? appeared first on Cryptonews.






