North Korea Weaponizes Blockchain for Stealth Hacks, Poses as Job Recruiters

North Korean menace group Famous Chollima is utilizing blockchain expertise to cover malware payloads in smart contracts, which marks the primary documented case of a nation-state actor adopting “EtherHiding” methods.
Cisco Talos and Google Threat Intelligence Group independently confirmed the assaults goal job seekers by pretend interview processes, deploying malware that steals crypto and credentials.
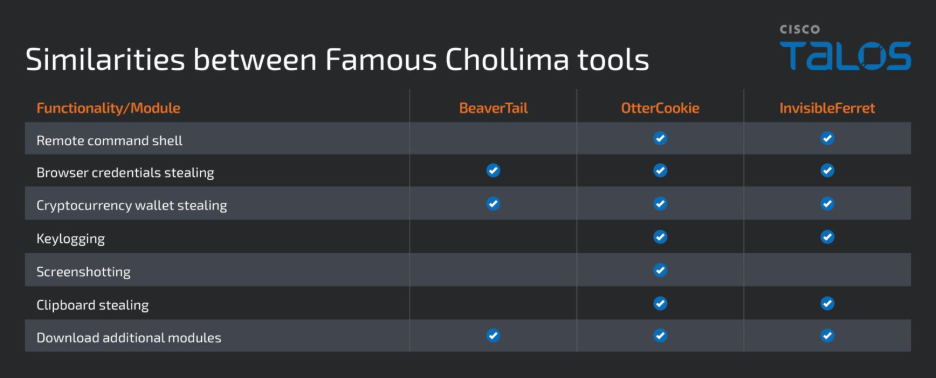
The group deployed a brand new JavaScript module that mixes BeaverTail and OtterCookie malware, that includes keylogging and screenshot capabilities.
The malicious software program was distributed through a Node.js bundle named “node-nvm-ssh” on the official NPM repository, disguised as a chess utility known as “Chessfi.”

Google has documented a North Korean group, UNC5342, which has been embedding JADESNOW malware and INVISIBLEFERRET backdoors inside good contracts on the BNB Smart Chain and Ethereum since February 2025.
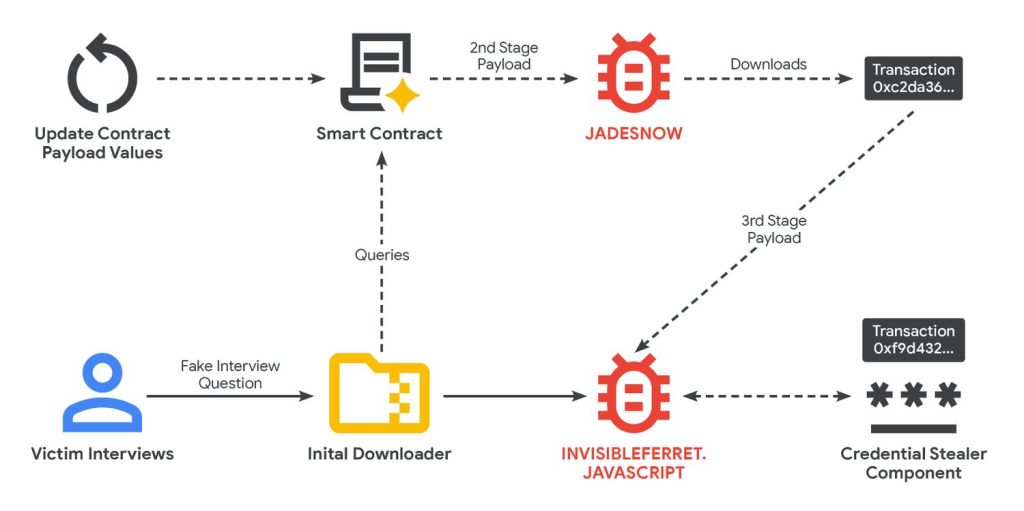
The approach shops malicious payloads on public blockchains, making a decentralized command-and-control infrastructure that can’t be taken down by regulation enforcement.
This discovery comes as North Korean hackers stole over $1.3 billion throughout 47 incidents in 2024 and $2.2 billion in the first half of 2025 alone, funding the regime’s weapons program by elaborate cash laundering networks.
EtherHiding Turns Blockchain Into Bulletproof Hosting Platform
EtherHiding embeds malicious JavaScript payloads inside good contracts on public blockchains, turning decentralized ledgers into resilient command-and-control servers.
Attackers retrieve payloads utilizing read-only perform calls that keep away from transaction charges and go away no seen blockchain historical past.
The approach presents decentralized storage, prevents takedowns, pseudonymous transactions obscure attacker identification, and immutable good contracts can’t be simply eliminated.
Attackers controlling contracts can replace payloads at any time, altering assault strategies or deploying completely different malware concurrently.
Google Threat Intelligence documented UNC5342 utilizing EtherHiding within the “Contagious Interview” marketing campaign, the place pretend recruiters impersonate corporations like Coinbase and Robinhood.
Victims obtain malicious recordsdata from GitHub repositories throughout technical assessments, triggering multi-stage infections.
The JADESNOW downloader queries BNB Smart Chain by API suppliers like Binplorer to retrieve payloads from good contract handle 0x8ea**8a71c.
The contract has been up to date over 20 instances inside 4 months, costing a median of $1.37 in fuel charges per replace.
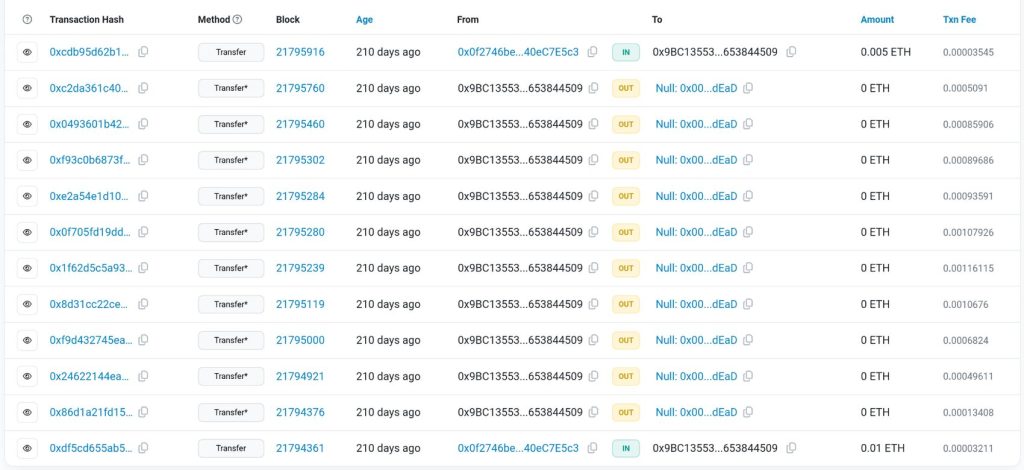
Blockchain explorers present on-chain transactions containing Base64-encoded and XOR-encrypted messages that decrypt to closely obfuscated JavaScript payloads.
The malware pivots between networks, querying Ethereum transaction historical past by a number of explorer APIs, together with Blockchair, Blockcypher, and Ethplorer.
The last INVISIBLEFERRET.JAVASCRIPT payload connects to command-and-control servers through port 3306, sending sufferer hostname, username, working system, and present listing.
The backdoor processes arbitrary command execution, file exfiltration, and listing harvesting whereas concentrating on over 80 browser extensions, together with MetaMask and Phantom.
Fake Companies and Stolen Identities
Earlier this yr, it was found that North Korean operatives established legitimate US corporations utilizing pretend identities to create credible company fronts.
Silent Push researchers found Blocknovas registered to a vacant lot in South Carolina, whereas Softglide traced again to a Buffalo tax workplace.
These corporations launched the “Contagious Interview” marketing campaign, a Lazarus Group subgroup specializing in malware deployment.
ZachXBT documented at least 25 instances of North Korean IT staff infiltrating crypto corporations, working beneath greater than 30 pretend identities with government-issued ID playing cards {and professional} LinkedIn accounts.
A compromised device revealed systematic expense documentation for buying Social Security numbers, skilled accounts, and VPN companies.
Last month, Binance founder Changpeng Zhao additionally warned about 4 main assault vectors, which embrace pretend job functions, fraudulent interviews with malware-laden hyperlinks, buyer help scams, and bribery of staff or outsourced distributors.
He cited a significant Indian outsourced service hack that leaked U.S. trade consumer knowledge, leading to over $400 million in losses.
Cisco Talos has beforehand documented Famous Chollima creating fraudulent skill-testing web sites utilizing React frameworks that intently mimic legit firm evaluation platforms by the PylangGhost malware marketing campaign, which targets crypto professionals.
Victims full technical assessments, which embrace downloading alleged video drivers containing malicious Python-based payloads.
Efforts have been made to cease these unhealthy actors, as U.S. authorities recently seized over $7.7 million in crypto allegedly earned by networks of covert IT staff.
The put up North Korea Weaponizes Blockchain for Stealth Hacks, Poses as Job Recruiters appeared first on Cryptonews.

 BNB (@cz_binance)
BNB (@cz_binance) 


